Sit cybersecurity threats 2025: stay ahead of the game

SIT cybersecurity threats encompass various risks, including phishing, malware, and ransomware, which can significantly impact businesses through financial loss, operational disruptions, and reputational damage.
Sit cybersecurity threats 2025 are looming over organizations, making it crucial to assess your protective measures. Have you thought about how these evolving threats might affect your operations? In this article, we will delve into what you need to know.
Understanding sit cybersecurity threats
Understanding sit cybersecurity threats is the first step in protecting your organization. These threats are constantly evolving and can come from various sources, including individuals and organized groups. The potential impact of these threats can be significant, affecting not just data security but also the very reputation of your business.
To grasp the essence of these threats, let’s explore the different types that are most prevalent today.
Types of Sit Cybersecurity Threats
There are several key types of threats that businesses should be aware of:
- Phishing Attacks: Cybercriminals often use deceptive emails to trick users into revealing sensitive information.
- Malware: Malicious software can disrupt operations and steal data.
- Ransomware: This is a type of malware that locks data, demanding payment for access.
As organizations adapt their strategies, the landscape of sit cybersecurity threats continues to change. For instance, many attacks now exploit weaknesses in remote work setups. Companies that have transitioned to remote or hybrid work models must pay extra attention to securing their systems.
Moreover, understanding the motivations behind these threats can help you anticipate and mitigate them. Criminals often target businesses with poor security practices or those that hold valuable information. By implementing robust security protocols and employee training, you can reduce your vulnerability.
Being aware and proactive is crucial. Regularly updating software, conducting security audits, and reinforcing employee education can make a substantial difference in protecting your business from these evolving risks.
Common types of sit cybersecurity threats in 2025
In 2025, understanding the common types of sit cybersecurity threats is essential for any organization. As technology advances, so do the tactics used by cybercriminals. Recognizing these threats will help you safeguard your business effectively.
Phishing Scams
One of the most widespread threats is phishing. These scams trick individuals into providing sensitive information through fake emails or websites. Cybercriminals often pose as legitimate organizations, making it crucial to verify the source before clicking on links or downloading attachments.
- Fake Emails: Look out for emails that seem unusual or have poor grammar.
- Cloned Websites: Always check the URL for legitimacy.
- Urgent Requests: Be wary of messages urging immediate action.
Next, we encounter malware, which includes various harmful software types designed to damage or gain unauthorized access to systems. This threat can infiltrate your devices through downloads or email attachments, causing data loss and system failure.
Additionally, ransomware has risen in popularity as cybercriminals seek to lock your files and demand payment for their release. Companies must have reliable backup solutions to protect against data loss from these attacks.
Other threats like DDoS (Distributed Denial of Service) attacks overwhelm a system’s resources, making it unavailable to legitimate users. This can harm businesses by disrupting operations and causing reputational damage.
Lastly, the human element remains a critical factor. Insider threats from employees, whether intentional or accidental, account for significant security breaches. Regular training and creating a strong security culture can help mitigate these risks.
Impact of sit cybersecurity threats on businesses
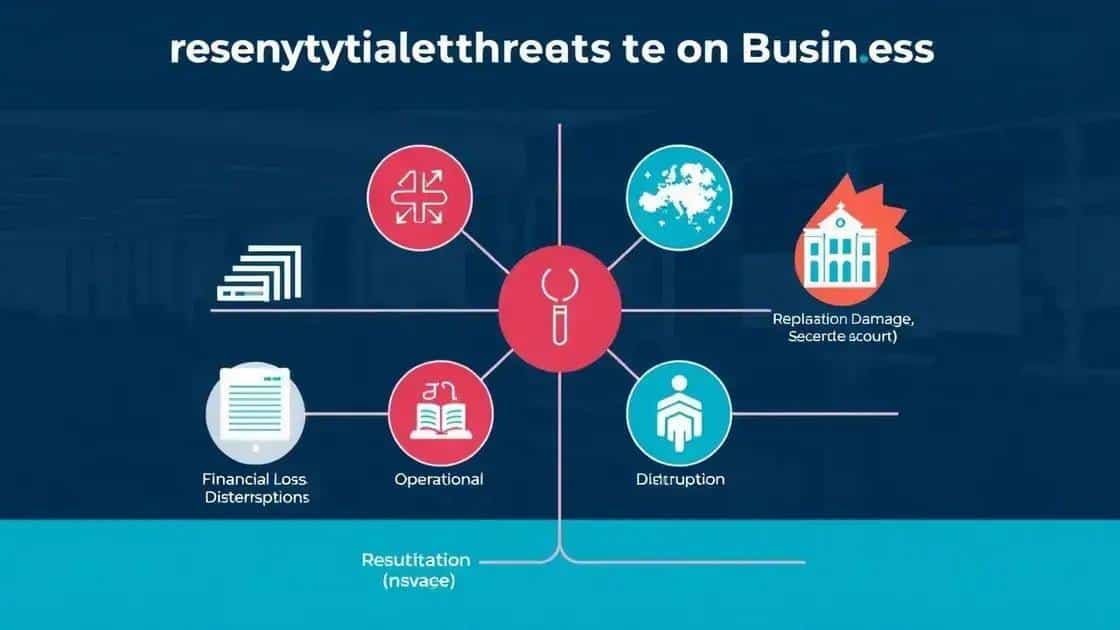
The impact of sit cybersecurity threats on businesses is profound and can lead to severe consequences. Organizations today face a variety of threats that can disrupt operations and damage their reputation.
One major consequence is financial loss. Cyberattacks can result in direct costs such as ransom payments, loss of revenue due to downtime, and expenses related to restoring systems. Beyond immediate costs, there are often long-term financial impacts, including regulatory fines and increased insurance premiums.
Operational Disruptions
Furthermore, businesses may experience significant operational disruptions. These interruptions can hinder productivity, causing delays in delivering products or services to customers. When systems go down, employees cannot perform their duties efficiently, leading to a ripple effect across the organization.
- Downtime: Time lost during a cyber incident can be costly.
- Recovery Efforts: Companies must invest resources in recovery, pulling staff away from their primary roles.
- Data Loss: Important data may be permanently lost, impacting decision-making.
Additionally, businesses that fall victim to sit cybersecurity threats may suffer from damaged reputations. Customers lose trust in companies that cannot protect their sensitive information. As a result, organizations may face a decline in customer loyalty, making it challenging to regain business after an attack.
Moreover, there are legal implications. Organizations can face lawsuits if they fail to protect customer data adequately. This legal risk adds another layer of complexity to managing cybersecurity, as companies navigate compliance requirements and potential ramifications.
Ultimately, understanding the impact of these threats is essential for businesses to prepare and implement effective security measures. By recognizing the potential consequences, organizations can prioritize their cybersecurity strategies and protect their assets more effectively.
Strategies for mitigating sit cybersecurity threats
Implementing effective strategies for mitigating sit cybersecurity threats is crucial for any organization. By taking proactive steps, businesses can safeguard their data and systems from potential attacks.
One fundamental strategy is to conduct regular security audits. These audits help identify vulnerabilities in a company’s systems and network. Knowing where weaknesses lie allows organizations to take corrective actions swiftly.
Employee Training
Another important aspect is employee training. Awareness programs educate staff on recognizing phishing attempts and other malicious activities. When employees are well-informed, they become an essential line of defense against cyber threats.
- Regular Workshops: Holding frequent training sessions helps keep security knowledge up-to-date.
- Phishing Simulations: Conducting tests can gauge employee readiness and prevent real attacks.
- Reporting Mechanisms: Establish channels for employees to report suspicious activities quickly.
Additionally, utilizing strong passwords and enabling two-factor authentication adds another layer of security. Strong passwords should be unique and complex, making it difficult for attackers to gain unauthorized access.
Regularly updating software and systems is also vital. Security patches and updates help protect against known vulnerabilities. Neglecting these updates can leave a business exposed to easily preventable threats.
Implementing a robust backup plan is essential. Regular backups ensure that if an attack occurs, data can be restored without major disruptions. Backups should be stored securely and tested frequently to confirm their effectiveness.
Finally, organizations should collaborate with cybersecurity experts. Partnering with professionals can provide insights into the latest threats and effective strategies to minimize risks. This expertise can help businesses stay ahead in the ever-evolving landscape of cybersecurity threats.
Future trends in sit cybersecurity threats
Understanding future trends in sit cybersecurity threats is vital for organizations looking to stay ahead of potential risks. As technology evolves, cyber threats will also adapt, presenting new challenges and opportunities for mitigation.
One significant trend is the rise of artificial intelligence (AI) in cyber attacks. Cybercriminals are beginning to utilize AI to automate attacks, making them faster and more sophisticated. This includes creating convincing phishing emails and launching targeted attacks, which can bypass traditional security measures.
Increased Mobile Vulnerabilities
As more employees work remotely and rely on mobile devices, there will be increased vulnerabilities. Mobile phishing attacks are likely to rise, making it essential for organizations to implement robust mobile security protocols. Ensuring secure connections and regular security updates will be crucial to protect sensitive data.
- Mobile Device Management: Implementing control over mobile devices helps mitigate risk.
- Regular Updates: Keeping software up-to-date minimizes vulnerabilities.
- User Education: Training users on mobile security practices is essential.
Moreover, we can expect to see more emphasis on data privacy regulations. Governments worldwide are tightening regulations to protect consumer data. This shift will require organizations to enhance their security measures and comply with new laws or face legal consequences.
Another emerging trend is the use of cloud services. While cloud storage offers benefits, it also introduces unique threats. Misconfigurations and insufficient security controls can lead to data breaches. Organizations will need to focus on cloud security and ensure that their data is well-protected within these environments.
Finally, the focus on holistic security approaches will grow. Businesses will increasingly adopt comprehensive security frameworks that integrate technologies and processes. This focus on collaboration and communication will enhance overall security resilience against evolving threats. Recognizing these trends early can empower organizations to invest in the right tools and strategies to defend against future risks.
FAQ – Common Questions About SIT Cybersecurity Threats
What are SIT cybersecurity threats?
SIT cybersecurity threats refer to risks and vulnerabilities that can compromise the security of systems and data in organizations, often exposing sensitive information to cybercriminals.
How can organizations prepare for future cybersecurity threats?
Organizations can prepare by conducting regular security audits, training employees on security awareness, implementing strong passwords, and ensuring software is always updated.
Why is mobile security important?
With the rise of remote work and mobile device usage, mobile security is crucial as these devices can be easy targets for phishing attacks and other cybersecurity threats.
What role does AI play in cyber attacks?
Cybercriminals use AI to enhance the effectiveness of their attacks, enabling automated phishing schemes and more sophisticated methods to breach security measures.





